If you tune into the news on any given day, chances are you will come across a story about a company that has suffered a data breach or has been compromised by crippling malware.
Unfortunately, these types of cybercrimes are gaining more and more momentum as businesses and organizations fall victim to phishing attacks. In just the last year, phishing attempts have grown 65% percent.
It’s very important to be able to recognize phishing attempts. We’ve put this article together in the hopes that it will educate and shed some light on what phishing emails are and how you can prevent them from infecting your computer and/or organization.
What is Phishing?
Phishing is a common scheme in which a cybercriminal will attempt to steal sensitive information such as credit card information, usernames, email addresses, and social security numbers by luring an unsuspecting user into providing the information willingly.
Phishing Emails
Cybercriminals typically mask themselves as legitimate people, businesses, or organizations to try and steal sensitive information from the user.
Usually, the cybercriminal will try to elicit fear, curiosity, and/or a sense of urgency from the targeted user, so that when they are prompted to open an attachment or fill in their sensitive information, they are likely to comply.
Here’s a real-world example of a phishing attempt we have seen at Miken Technologies. This email was sent to a client under the disguise of “WordPress” – a website content management system that the client utilizes for their business website.
This email states that there was an unauthorized successful login attempt to the client’s website coming from India. The email continues to say that there is a risk and that the client must update their information.
Right away, there are a few things ‘off’ about this email.
- Punctuation is bad within the email as well as the subject line. There are missing spaces between words and commas, as well as the use of lowercase lettering at the beginning of the second sentence when it should be uppercase. An email like this would never make it past an editor at a large company such as WordPress.
- Poor graphical execution on the “WordPress” logo itself. It is comically large.
- Take a look at the senders. These are clearly not coming from WordPress.

We’ve also seen examples of phishing emails coming from a trusted vendor that a business uses. These phishing emails will typically contain an attachment, such as an invoice for example. The attachment essentially ‘opens the door’ for the cybercriminal to then access the user’s machine to install malicious content, steal data, or access the entire network infrastructure.
Below is another real-world example of a phishing attempt we have seen. This particular individual received an email from a cybercriminal posing as a trusted vendor sending an invoice.
Sensitive information has been redacted, but you can see how this email would look legitimate to someone working in the accounting department. It appears to be coming from a trusted vendor, with a dollar amount and attached invoice.
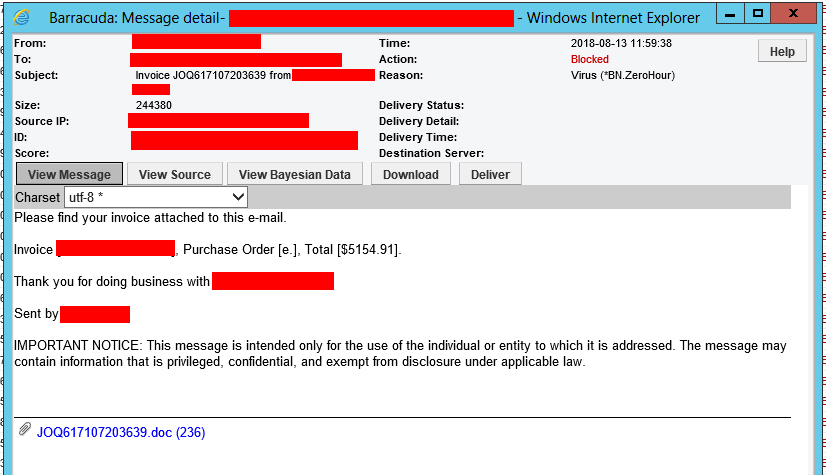
It’s important to ask yourself: “Am I expecting anything from this person/company?”
If you’re unsure, then it’s important to verify the legitimacy of the email. Never reply directly back asking “Is this legitimate?” because the criminal spoofing the email can simply reply back “yes.”
To recap: below are 5 Ways to Identify Phishing Emails.
- Check the sender’s email address: Cybercriminals will often create email accounts that closely resembles a company’s official email address. Or, in some cases, such as the WordPress example above, they won’t even go through the trouble of hiding their email address.
- High sense of urgency: In most cases, a high sense of emergency will be included in the body of the email. “Your account has been hacked, click here to reset your password” for example is just a way for you to act quick without hesitation.
- Links to fake websites: Just about all phishing emails will contain some form of ‘Call to Action.’ This could be a simple ‘click here’ link or an attachment containing the malicious code. Hover your mouse over the link (Do NOT click it!!) to see where the link is coming from.
- No personalization: In most cases, cybercriminals will send out hundreds or thousands of phishing emails at once. Going back to the WordPress example above, you can see that the email starts off with “DearUser” which is not only very generic, but also lacks proper punctuation. Which brings us to our final point…
- Poor grammar and punctuation: Does the email containing misspellings, poor punctuation, and poor grammar? Then it’s most likely a phishing email.
*If you have received an email that you are questioning the legitimacy of, please do not hesitate to send it to Miken for review. It’s also important to verify from the sender that the email is legitimate.
If you would like more information on phishing, please contact us!








